Computer users around the globe are being hit by a new kind of virus that freezes their computer and accuses them of committing heinous crimes, like distributing child porn. The threats sound real enough that victims are coughing up $200 to pay a "fine," and virus writer gangs are netting millions, security firms say.
The message that flashes across infected computer screens sounds downright scary:
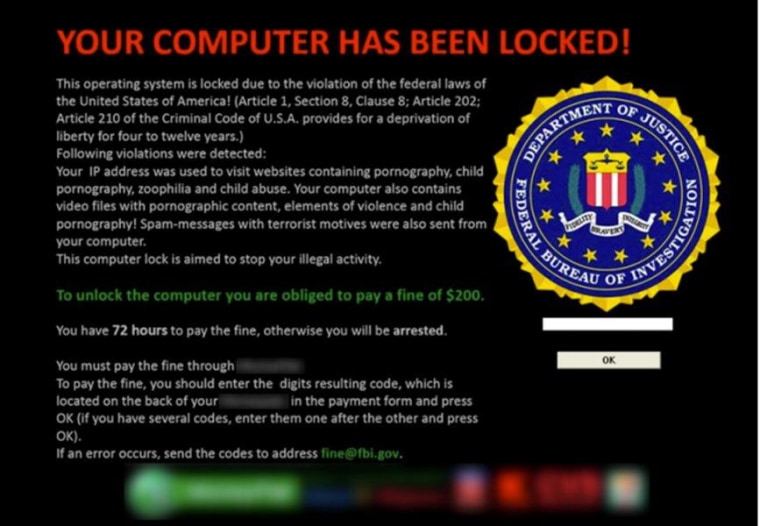
"You have been viewing or distributing child porn ... violating article 202 of the Criminal Code of the United States of America," says one version, allegedly sent by the FBI. A virus victim supplied the message to NBC News.
In each case, the accusation appears on a pop-up screen while the virus simultaneously disables the computer. The message often shows the user's IP address and city, and sometimes, recent websites visited by the victim. The most alarming version activates the victim’s webcam, takes his or her picture, and displays it on the warning.
"They are saying, 'we know who you are, where you are, and what you were doing,'" said John Harrison, a security researcher with Symantec. "They attempt to scare the heck out of you."
The victim is then offered an option: pay a fine within 72 hours, and the charges will be dropped, while the computer will be restored.
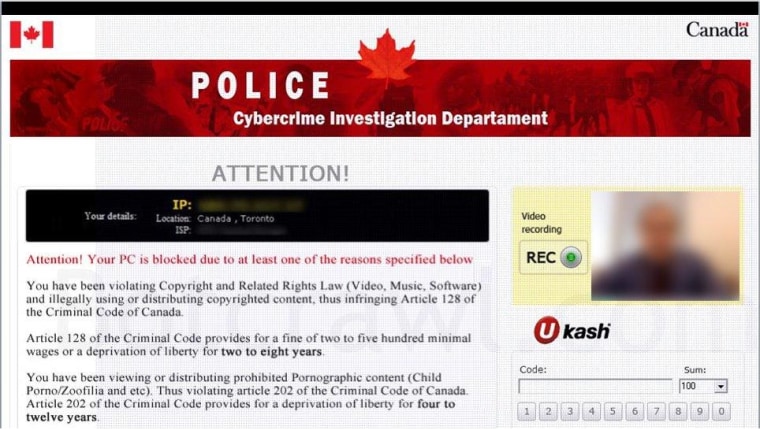
The malicious software is so cleverly crafted that it comes with 30 to 40 versions packed inside. It displays in the appropriate language for victims — English, Spanish, Russian, etc. — and invokes the local federal authorities. A U.S. victim might get a notice from the FBI's Internet Crime Complaint Center, while a Canadian victim gets one from the Royal Canadian Mounted Police.
The message is fake, of course — and even those who pay the "fine" still have a broken computer. But victims worldwide are falling for it. Harrison said for one version he tracked, roughly 3 percent of victims actually paid up. The criminals behind that virus netted $5 million, Symantec estimates.
With results like that, other virus gangs have been quick to copy the profitable formula. Symantec believes that gangs who spent the past couple of years making money tricking consumers into paying for fake antivirus software have all taken up the fake criminal charges and fine scam.
"So many of these folks have jumped on the bandwagon," Harrison said. "They have really transitioned into this."
The general technique is called ransomware — a virus disables the computer, allegedly holding it hostage until a ransom is paid — and it's not new. But the clever combination of an abrupt interruption, the localization trick, and the severity of the accusation catches many victims unaware, and they let their guard down enough to pay the fine.
There are no hard numbers on the frequency of ransomware, but there's plenty of anecdotal evidence it's on the rise. In February, Europol busted a multi-national crime ring involving a Russian programmer arrested in the United Arab Emirates, and 10 others arrested in Madrid, Spain. There were victims across 30 countries. Authorities in Spain said 700,000 Spaniards had contacted the government asking for help after becoming infected.
The agency issued another warning about the scam on April 11.
“Fraudsters are deploying extortion techniques using Europol's identity and logo to con EU citizens out of money,” the warning says. “Variations of this con, using the identities of other international and European agencies, are also in circulation.”
It's possible the problem is even worse than security firms realize, because many victims may not be reporting the infection, Harrison said.
"If you were at work and there was a message on your screen that said you were viewing child porn, would you run to get your IT department?" he said.
Most victims pick up the virus by visiting booby-trapped web pages that surreptitiously install software on victims' machines through "drive-by” download, or by downloading free software from disreputable sites. In fact, some variations of the virus accuse victims of violating copyright law, knowing that is likely true.
Victims shouldn't pay the fine, Harrison said, but they should know that various software tools — including free tools available at Symantec — can rid their machines of the virus.