WASHINGTON — In 2015, when the news broke that the Pentagon had mistakenly shipped samples of live anthrax virus around the world, officials immediately faced tough questions from reporters. A review was ordered. The military equivalent of a grand jury investigation was launched into the question of leadership failures.
This week, the fruits of another risky American government experiment wreaked havoc, but the response was much different.
A sophisticated cyber attack disrupted companies and governments in the U.S. and abroad. The malware used in the attack capitalized on vulnerabilities in Microsoft's operating system that had been stockpiled by, and were stolen from, the National Security Agency, former NSA officials told NBC News. Dubbed Petya by some, the attack was similar to the WannaCry virus, which spread in May to 150 countries and was also developed to attack a software flaw revealed in an NSA leak, former officials said.
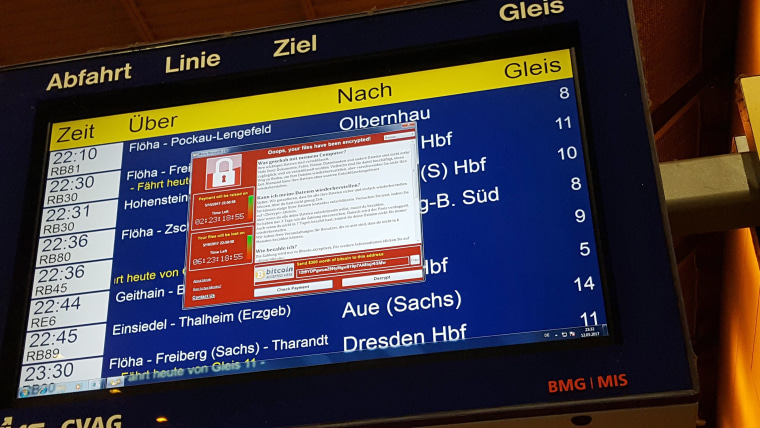
At the NSA and the CIA, government hackers secretly collect and store software flaws that they later exploit to spy or inflict damage on America's adversaries. But those same weaknesses can be turned against almost any machine — and are hard to control once loosed on the internet. In that sense, they are the cyber equivalent of biological contagions. And lately, the U.S. government has proven itself unable to keep its cyber weapons secure.
Related: Paying Off Petya-Variant Ransomware Won't Unlock Your Files
Yet, so far, no one from the NSA or the CIA has said a word in public about the situation. The Trump administration has not addressed the American role in the origin of the malware. And it's unclear whether anyone in the U.S. intelligence community has been held accountable for the latest in what has been a string of breaches that compromised dangerous U.S. hacking tools.
The Petya and WannaCry attacks exploited vulnerabilities made public by a group calling itself the Shadow Brokers, which first released them in April. It's unclear how the software flaws were stolen from the NSA.
That followed a breach in March at the CIA, when WikiLeaks claimed that it had obtained a trove of CIA hacking tools after the vaunted spy agency had lost control of its entire arsenal of cyber weapons. That may have been an overstatement by WikiLeaks, but a number of CIA techniques were made public — and no one has yet explained how that happened or what has been done to prevent it from happening again.
Such thefts leave spy agencies in an untenable position, said Michael Hayden, a former director of both the CIA and the NSA.

"If American espionage cannot protect the special tools that it possesses, it doesn't matter that they are good people working for good purposes under good oversight," Hayden told NBC News. "If they cannot protect the tools, I just can't mount the argument to defend that they should have them. This is the one that, unless resolved, I think actually could constitute a legitimate argument to do less."
Officials at the NSA, the digital spying agency that is known for its unwillingness to deal with news media inquiries, did not respond to requests for comment. At the CIA, which has never been shy about engaging reporters, spokesman Ryan Trapani obliquely defended the agency's cyber espionage operations, without speaking directly to the leak or its implications.
"CIA's mission is to aggressively collect foreign intelligence overseas to protect America from terrorists, hostile nation states and other adversaries," he said. "It is CIA's job to be innovative, cutting-edge, and the first line of defense in protecting this country from enemies abroad."
Related: WannaCry Threat Remains, Say Experts
He added, "We have no comment on the authenticity of purported intelligence documents released by WikiLeaks or on the status of any investigation into the source of the documents," but that "the American public should be deeply troubled by any WikiLeaks disclosure designed to damage the intelligence community's ability to protect America against terrorists and other adversaries."
Former senior NSA officials offered a defense of the agency on condition of anonymity, because they are not authorized to discuss their prior work.
One former official told NBC News in May that the NSA releases 90 to 95 percent of the software vulnerabilities it discovers, but it sits on the rest for use in hacking and spying activities. In other words, the agency doesn't tell Americans about software holes that make them vulnerable — so it can exploit those weaknesses to spy on foreigners.
Some people would like the NSA to alert industry to every software hole it finds. But then, the former official said, the NSA would lose avenues for spying and attack. And hackers would still find holes to exploit, because such holes are inevitable.
"We do have software vulnerabilities out there, and why shouldn't the NSA be in the business of helping to protect us by exploiting those things when necessary?" a second former official asked.
But one thing neither former official could answer is why the NSA has continued to experience major breaches of classified material. First former NSA contractor Edward Snowden leaked some of the most sensitive secrets ever made public. Then another contractor, Harold Martin, was accused of taking home reams of classified documents. Then the Shadow Brokers obtained the software flaws.
Through it all, the same person, Kemp Ensor, has been head of security at the agency, according to his LinkedIn profile. The NSA did not respond to a request to make him available, and he did not respond to a message sent through LinkedIn.
The success of the cyber attacks can't be blamed entirely on the U.S. government. After it learned of the Shadow Brokers leak, the NSA warned Microsoft and other companies, the former officials said. Microsoft released a patch in March designed to fix the flaw.
But many companies and individuals failed to patch their systems. Those running outdated software may not even have been be able to.
After the WannaCry attack in May, Microsoft general counsel Brad Smith took direct aim at U.S. intelligence agencies.
"This attack provides yet another example of why the stockpiling of vulnerabilities by governments is such a problem," he wrote in a blog post. "This is an emerging pattern in 2017. We have seen vulnerabilities stored by the CIA show up on WikiLeaks, and now this vulnerability stolen from the NSA has affected customers around the world."
He continued, "Repeatedly, exploits in the hands of governments have leaked into the public domain and caused widespread damage. An equivalent scenario with conventional weapons would be the U.S. military having some of its Tomahawk missiles stolen."
