LONDON — While Americans are just coming to terms with the prospect of political cyberattacks tied to Russia — it isn’t the first time Kremlin-linked hackers have been accused of trying to influence voters in other countries.
A torrent of stolen emails released by WikiLeaks — most damaging to the Democrats and Hillary Clinton — have marked the 2016 race in what U.S. intelligence officials say is an unprecedented attempt to by Vladimir Putin's government to undermine trust in the U.S. election process.
"Anytime you have a geopolitical conflict now you see its reflection in cyberspace"
"We believe, based on the scope and sensitivity of these efforts, that only Russia's senior-most officials could have authorized these activities," the Department of Homeland Security and the Office of the Director of National Intelligence said in an extraordinary gloves-off statement on Oct. 7.
Russia has been accused of this before, notably when hackers attempted to hijack an election in neighboring Ukraine in 2014.
A few days before the vote, a sophisticated cyberattack shut down Ukraine’s Central Election Commission’s computer systems by disrupting the internal network. A pro-Russian hacktivist group called CyberBerkut claimed responsibility for the attack.
CEC administrators were able to restore the system in time for the vote, but on election day the website was compromised again when a photo was posted falsely showing a far-right candidate had won the vote. Russian state television went on to broadcast an image allegedly taken from the site to report what turned out to be a false story.
Related: The Russian-Backed Hackers Attacking the U.S. Political System
It is not clear whether CyberBerkut was responsible for the false photo, or if other hackers were involved.
But according to a Ukrainian official investigating the incident who spoke to NBC News on condition of anonymity as the investigation into the incident is ongoing, additional malware was found on the election commission's system. This was traced back to the group APT28, also known as Fancy Bear which has been linked to the recent hacks in the U.S.
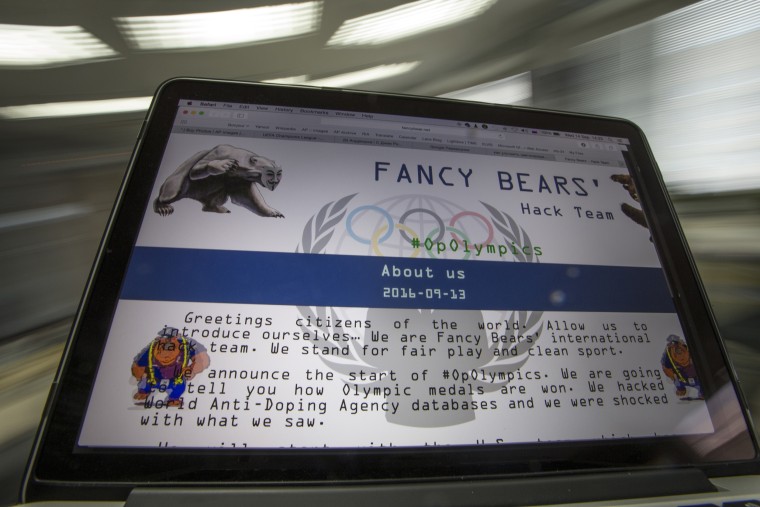
While the 2014 incident did not alter the outcome of Ukraine's elections, the hackers accomplished their goal, according to NATO cyberdefense ambassador Kenneth Geers.
He believes the hack was a Russian attempt to discredit the election and “muddy the waters.”
“Maybe the goal was just to disrupt the process and its integrity or credibility,” he told NBC News, adding that the timing of the attack was critical.
Ukraine was electing a new leader to succeed pro-Russian Viktor Yanukovych, who had been forced out of office by the Euromaidan street protests that erupted in Kyiv in late 2013.
Russia had already annexed the Crimea region from Ukraine and a Russian–backed separatist movement was waging an armed insurgency in the east. And the battle on the ground was also being fought online.
“Anytime you have a geopolitical conflict now you see its reflection in cyberspace,” Geers said.
At the time Russia said it had no role in the hack, just as it has rejected accusations that it is trying to meddle in the American presidential race.
"We deny it completely," the Kremlin's top spokesman Dmitry Peskov told NBC News when asked whether his government supported hackers trying to influence the outcome of the U.S. election.
Related: Putin Denies Meddling in U.S. Election
But Christopher Porter, an analyst with the cybersecurity firm FireEye, says the attacks in Ukraine and in the United States fit a pattern.
“Something we’ve seen in [the U.S.] election is a close tie between APT28 activities and social media and broadcast news outlets in Russia,” he said. “As soon as they release a new leak or at the same time or beforehand they will have a news story all ready to go.”
The U.S. documents stolen in the recent attacks were released through WikiLeaks and pushed out almost simultaneously on Russian news sites.
FireEye researchers have linked APT28 to Russia in part by showing that some of the source code was written in Russian and that malware was compiled during Russian working hours.
Malware associated with APT28 has also reportedly been found on the computers of German lawmakers earlier this year in what investigators describe as an espionage campaign, according to an IT security researcher who investigated the attack on behalf of a political party there.
APT28 also claimed responsibility on its website for leaking athletes' health records from the World Anti-Doping Agency database in an apparent attempt to discredit the organization after it recommended Russian athletes be banned from this year’s Rio Olympics.
While breaches in the U.S. have been more embarrassing for the Democrats and Clinton, the intent of Russia’s alleged meddling was not to favor a particular candidate but to “undermine democracy in some vague way” and “sow discord,” Porter said.
Donald Trump and his supporters have repeatedly claimed the election is rigged while pointing to documents published by WikiLeaks. This may be just the kind of “discord” the attackers had planned.
And there may be more to come.
U.S. intelligence officials are concerned that attackers with ties to Russia could try to post falsified documents to try to undermine confidence in the result and to stir fears of voter fraud.
U.S. officials already sent warnings to Illinois and Arizona in August after reports that hackers had infiltrated voter registration rolls in those two states, though it was unclear what, if any, information was obtained or altered.
A huge amount of data about U.S. voters is already being offered for sale online, experts warn.
Related: U.S. Confident It's Blocked Russia's Hacking Paths
“We saw 190 million national records for sale in October 2015 for $20,000,” said Porter, the cybersecurity analyst.
The voter information appears to be a combination of public data that was easily acquired to other records that were more likely illegally obtained, according to Porter. It is not clear how attackers could use this information.
While senior U.S. officials maintain the Russian state is behind the slew of cyberattacks in the U.S., a leading Moscow-based cybersecurity expert said he doubted that the Kremlin was really responsible for the latest spate of hacks.
Oleg Demidov, a cybersecurity consultant with Moscow-based policy center PIR, told NBC News that he had not seen hard proof of Russian state involvement.
Concerning the possibility these hacked databases could be used to damage an election campaign he said: “I do not see it.”
U.S. officials also have said it would be extremely difficult for anyone — including state-backed hackers — to alter the actual ballot count in the U.S. election, or to get into the actual voting machines.
Still, FireEye's Porter warned Russian hacking groups have shown they have firepower beyond just hacking databases and websites. He noted as an example the unprecedented cyberattack on a Ukrainian power distributor just before Christmas last year that temporarily knocked out electricity to 230,000 people.
“The Russian government-backed ... groups are limited by their will, not by technology,” Porter says. “They can do a lot more damage than they’ve currently done.”
