Even if you pay off the new globally spreading ransomware, you won't pull the plug on the malicious software.
There's no way for the hackers to communicate with victims who find their files locked up. Early Tuesday morning, the email address listed in the ransomware was blocked, the Posteo mail provider told NBC News in an email.
"Our abuse-team has blocked the account very early today," Posteo co-founder Sabrina Löhr said. "We are in contact with the Federal Office for Information Security here in Germany to make sure that we react properly."
Related: Widespread Cyberattack Hits Major European Companies
But that doesn't mean the computer worm will stop spreading. And it also means there's no way way for the cybercriminals to send unlocking codes to people who pay the $300 bitcoin ransom — assuming they ever intended to live up to their part of the bargain, security researchers told NBC News.
"If Posteo killed the address, people paying and then emailing them to retrieve decryption assistance will not receive it," said Paul Burbage, a malware researcher for Flashpoint Intelligence, which analyzes security issues for NBC News.
Despite this, the electronic currency wallet listed in the red-text-on-black-screen ransomware notice continued to receive funds Tuesday afternoon. As of 6 p.m. ET, the wallet's value was up to nearly $8,000.
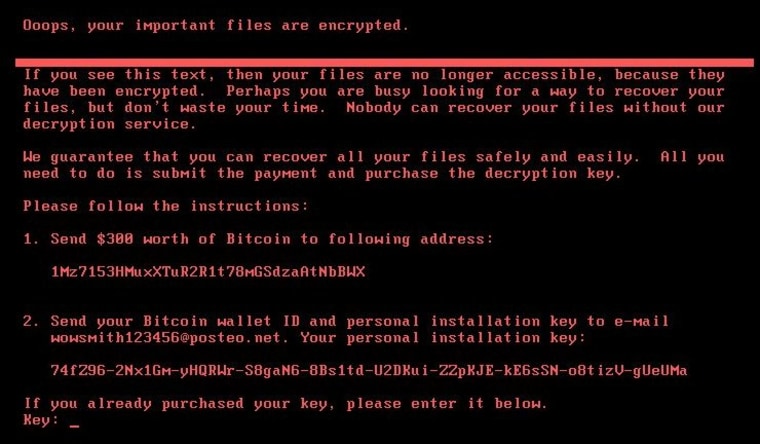
More than $120,000 was sent to hackers during the previous "WannaCry" global ransomware attack.
Initial reports indicate the new infection hasn't spread as much as WannaCry, but it did reach a large number of organizations. Kaspersky Lab's analysts report 2,000 infections so far. Any computers that hadn't been updated to patched for Wannacry based on the National Security Agency's leaked "EternalBlue" exploit could be susceptible. The security firm Symantec said it had confirmed the new malware used the EternalBlue flaw.
Researchers say all companies should update and patch their Windows software immediately, ensure that they backup and have installed ransomware detection.
If you know your computer is infected, don't restart your computer or pay the ransom, Ryan Kalember, senior vice president of cybersecurity for Proofpoint, told NBC News in an email. If your computer has already restarted, the best option is to restore it from a backup, he said.
Wannacry was discovered to have an internet "kill switch" that allowed infected computers to be unlocked without paying. Initial analysis by researchers shows that this latest strain of computer infection doesn't need internet connectivity and may not have such a kill switch.
Several security researchers said they believe the current ransomware attack is using malicious software, or malware, based not on "Wannacry" but one another one called "Petya," the Russian word for "Peter." However Kaspersky Labs says it may be an entirely new piece of software.
Russian language criminal message board posts have been spotted asking "what's the best ransomware," and respondents recommend looking at Petya.
MeDoc, the official accounting software of the Ukranian government, acknowledged that there were reports that its software was exploited as what's called the initial attack vector, but it said its latest service pack update, dated June 22, was not infected.
Wherever the infection started, infected systems were able to send the ransomware "loader" to other machines in a network when the computers checked for software updates, Flashpoint said.
And if it is indeed a Petya variant, it would attack via by spam emails with infected documents attached, as well as through neighboring infected computers, researchers said. The code would then target the master boot record of a drive, going on to create its own "miniature operating system" and encrypt the rest of the files.
While WannaCry targeted only the files, Petya encrypts the "master file table." That's sort of like locking the card catalog of the hard drive. If you can't open the card catalog, you can't find where your books are.
Despite the Russian name and the Ukranian focus of the initial attack, researchers said they think that it's unlikely that the attack is state-sponsored.
"A state actor won't specifically use an exploit that is already distributed. It's not likely it's a state actor, more likely someone from a cybercrime organization," said Itay Glick, chief executive of the Israel-based cybersecurity firm Votiro.
Cybersecurity experts say all it takes is for one person to open a malicious document to take down an entire computer network.
"Today's attack hit critical infrastructure — finance, transportation, manufacturing and more," Michael Kaiser, executive director of the nonprofit National Cyber Security Alliance in Washington, D.C., told NBC News in an emailed statement. "It is our shared responsibility to do our part in keeping devices secure. It all starts with basic cyber hygiene around software updates and locking down logins."
