"I really worry about everything going to the cloud," Apple co-founder Steve Wozniak recently said. "I think it's going to be horrendous. I think there are going to be a lot of horrible problems in the next five years."
Wozniak spoke about the trouble with cloud computing on Saturday, according to the Agence France-Presse's Robert MacPherson. On Monday, Wozniak's frustrations with this technology became clearer, when he explained — in a post on Gizmodo — that he'd recently lost one of his Google calendars, thanks to a third-party app he'd authorized to handle an upgrade. On Friday, Mat Honan, a prominent tech reporter, discovered that his account on iCloud — Apple's cloud storage service — was compromised. And just a few days before that, the popular cloud storage service Dropbox revealed that some of its users' accounts were accessed after a security breach. In short, it's a jungle up there.
Of course there's more to each story — isn't there always? — but no matter where most of the blame lies for each security incident, the end result is the same: Someone's most precious digital asset, his or her data, was either lost or laid bare before someone who shouldn't ever see it, much less touch it.
That doesn't mean victims are clueless, far from it. But little messes can happen due to laziness, blind faith in third-party services, flaws in security procedures, trust in the people nearby or what some call "social engineering" — good ol' fashioned con artistry.
A brilliant tech executive uses a gesture password so simple that I memorized it after seeing him reach for his phone just once, another left his unlocked phone sitting right next to me, another didn't even bother to use any sort of password on his device. One of the smartest editors I know never bothered to learn about security features available on his email service until today, another uses "1111" as his iPhone password, another has his "most secure" password written on a sticky note which sits in his wallet.
I think you get the idea.
So what should you do to avoid being another one of these smart people to whom a bad thing could easily happen? You shouldn't allow yourself to be a lightning rod in the middle of the cloud.
Sorry. The cheesy line was irresistible — but true. Perhaps not every single incident which occurred in the last week could've been prevented, but the risk of it could've been significantly lowered if the users took a couple of precautions.
Start with passwords so strong that they can throw you across the room
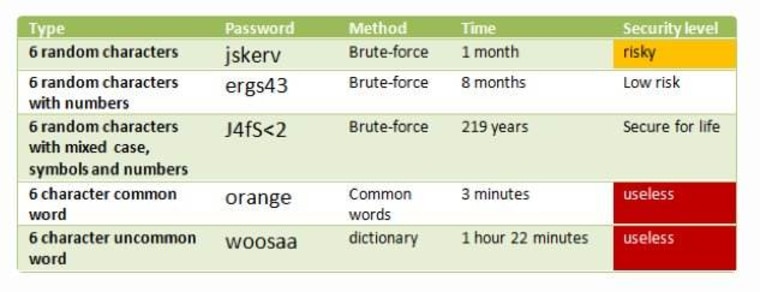
We've all had it drilled into our heads that we should use long passwords which incorporate (upper- and lower-case) letters, numbers and symbols, but are those really the best choice?
Not exactly, according to some number-crunching done by security expert Thomas Baekdal a few years ago.
As you can see by the chart above, complex passwords — like the ones I just described — are in fact pretty darn secure. In theory, such a passwords would take a hacker over 100 years to discover if he or she were using an automated system capable of systematically guessing 100 passwords per second.
But how long would it take you to regularly memorize a password that looks as if it was created by a squirrel who danced across a keyboard after drinking twenty cups of coffee? Long enough to make you think twice about creating a complex password, right?
So how about using secure passwords which consist of easy-to-remember, multi-word phrases instead?
Such phrases — which can include things like "this is fun" or "fluffy is puffy" — are even more secure than the complex passwords which you may or may not memorize easily. In fact, Baekdal suggests that math shows "this is fun" to be ten times more secure as a password than "J4fS
If you don't have faith in this approach to password selection though, at least keep in mind that, no matter what they say, size does matter. Longer passwords are more difficult to crack, even if you're not using strange characters. But because they increase the combination possibilities dramatically, using strange characters — such as parentheses, exclamation marks, or even spaces — can mean the difference between a secure and a compromised password of the same length.
Remember that two layers of security are better than one
Many services, such as Google and (as of recently) Dropbox, offer two-factor authentication. This means that you can set your accounts to require a regular password as well as an authentication code, which is either generated by an app or texted to your phone. Such a system is fantastic. It means that if your password is somehow compromised, your account can still remain safe. (Unless your phone is snatched as well, of course.)
I have yet to come up with a reason to not use two-factor authentication on every service that offers it and I strongly urge you to turn it on. In the case of Mat Honan, the reporter who was hacked recently, that simple action might have prevented a lot of additional damage. It's hard to say how much, though, because Apple doesn't offer such a security feature on iCloud yet.
An app for every password and a password for every app
Some services — I'm once again nodding at you, Google — offer app-specific passwords. This means that you can generate a fresh password for every third-party app. If something goes wrong, you simply de-authorize that app in your account settings and get on with your life — no fuss, no muss.
There are plenty of password manager applications which will do the same thing for you, albeit they can have some drawbacks. (You are basically creating an extra point of failure, after all.)
One of the most popular password managers around is called LastPass, but unfortunately its reputation suffered after a possible security breach in May 2011. But no worries: Lifehacker's Whitson Gordon explains that while LastPass is still trusted and favored by many, there are several alternatives such as KeePass, 1Password, or Keeper.
Don't double-dip
I know it's so tempting to use the same password for multiple websites or services — oh-so-very tempting — but you must resist.
Let me repeat that in case you were just skimming this article: Do. Not. Reuse. Passwords.
Nearly every single time a site or service suffers some sort of security breach, we read about folks who have unrelated accounts compromised — simply because they used the same log-on information for them. This is one of the easiest vulnerabilities to prevent, so please don't let laziness get the better of you.
Ch-ch-ch-ch-changes
Change your passwords. I know it's not fun to find yourself fighting against muscle memory and entering the same password five times before realizing that you changed it yesterday and then throwing your phone across the room because you're locked out of an account for 24 hours and then — ahem.
Just change your passwords on a regular basis. Not as often as your underwear, but not as infrequently as your smoke detector's batteries.
Forget about your first pet
Your middle name. Your mother's maiden name. Your first pet's name. Your favorite teacher's name. Those are all things someone can discover by asking enough questions or by getting creative with some Google searches.
Don't use them as answers to security or password recovery questions. If whatever service you're using doesn't allow you to write your own question, then just come create a system to confuse any creative guessers. Try alternate spellings, make a mental note that you always answer questions about your "favorite pet" with your favorite line from a song or similar.
You're only as strong as the weakest link
When hackers took over Mat Honan's iCloud account, he was in deep trouble. Not only could the account be used to remotely erase his iPhone, iPad and MacBook, but it also happened to be associated with his Gmail account. Honan set up his Gmail account to send emails with password reset instructions to that very iCloud account. He guarded a reasonably secure account with one that was vulnerable.
I don't need to tell you how that ended.
"Make sure the back-up email account you list has good defenses so it can't be used to request an unauthorized password reset on your main account [and] list a phone number when possible because it is often the fastest, most secure way to recover your account when you need it," suggests a Google spokesperson after hearing about that situation.
Keep your accounts as separate as possible — if you can avoid daisy-chaining things, do so. Send password reset instructions to your mobile device. Send them to a very trusted friend's mobile device. Send them to your mom.
Unfortunately, sometimes there are weak links which sneak in without any mistakes on a user's part. In Honan's case, someone managed to get information which could be used to reset that troublesome iCloud account in the first place by taking advantage of a completely unconnected Amazon account belonging to Honan.
Don't surrender too much control
As lovely as it can be to hand the controls to someone else and not worry about anything occasionally, the whole arrangement can easily get you in trouble. Do you really want the person who manages to compromise your iCloud account to have the ability to remotely erase your computer? To erase your system backups? Because he or she could indeed do this if you happen to have "Find My Mac" toggled on.
In Mat Honan's case — which is unfortunately becoming a frightening cautionary tale— the feature wasn't even that useful, as he explains in a piece on Wired:
I shouldn’t have used Find My Mac. Find My iPhone has been a brilliant Apple service. If you lose your iPhone, or have it stolen, the service lets you see where it is on a map. [...] But as a friend pointed out to me, while that service makes sense for phones (which are quite likely to be lost) it makes less sense for computers. You are almost certainly more likely to have your computer accessed remotely than physically.
You can run, but you can't hide
Here's the thing. You can follow every single tip written above to the letter and spirit — and your beloved online accounts could still get compromised, data could get lost, information could get leaked. There's always some overlooked detail, some flaw in a service, some stupid mistake.
So just remember to keep backups — physical, local backups — and to only trust the Internet as far as you could throw it.
Want more tech news or interesting links? You'll get plenty of both if you keep up with Rosa Golijan, the writer of this post, by following her on Twitter, subscribing to her Facebook posts, or circling her on Google+.
