After investigators of a child pornography ring were found to have compromised Internet anonymity service Tor in August, it was revealed Friday that the NSA, too, has its sights set on the network, and have set sophisticated digital traps to ensnare its users.
The information regarding the Tor surveillance programs was detailed in top-secret documents leaked by Edward Snowden. Security expert Bruce Schneier explained the attacks in a column at The Guardian — but even technically minded folks may find the alphabet soup of acronyms, protocols and secret programs confusing, so we've extracted the main points.
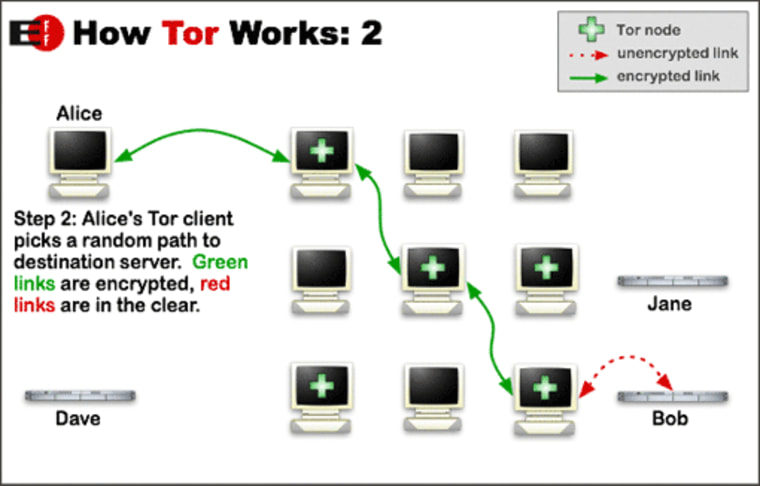
Tor works by taking traffic from one user and passing it between other users of the network, changing the data's path through the Internet constantly and providing effective anonymity. It's so effective, in fact, that the National Security Agency can't actually track someone using it — so it had to find a way to get around it.
What the NSA did was set up what is known as a "man in the middle attack." First, it closely monitored known Tor "exit nodes," where anonymized traffic emerges from the Tor network, waiting for users looking to do a basic task like visit Google. Then, by using the agency's access to Internet infrastructure to respond before Google can, NSA agents would redirect the user's browser to a special webpage where a trap would be sprung.
The secret documents describe a system of servers collectively called "FoxAcid," which Schneier describes as "a matchmaker between potential targets and attacks developed by the NSA." Browsers with known flaws can be sent to Web pages that are custom-designed to infect them — it only takes a fraction of a second, and then the user can be sent on their way.
Since the browser is now compromised, it can be made to do all kinds of things: report browsing history, IP logs, or even inform on other nodes in the Tor network.
By attacking the browser itself, the NSA doesn't have to worry about the strong protection offered by Tor. Firefox fixed the flaw used in the case of the child pornography investigation, but undocumented bugs or vulnerabilities may exist in any Web browser or plug-in, which the NSA could exploit for its purposes.
For a more complete and technical explanation of FoxAcid and related NSA Internet surveillance programs, be sure to read Schneier's article at The Guardian.
Devin Coldewey is a contributing writer for NBC News Digital. His personal website is coldewey.cc.
