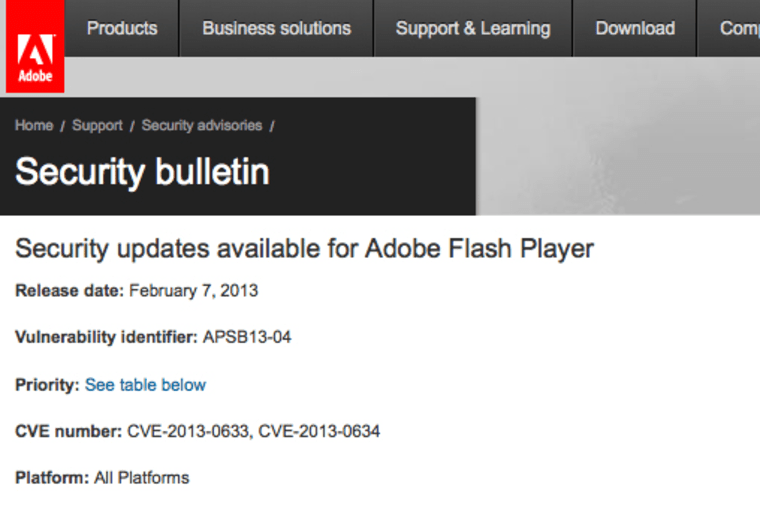
Adobe wants Windows, Mac and Linux users to install a critical security update, issued Thursday, for Adobe's Flash Player. Without it, the company says, there are vulnerabilities in the program that could "cause a crash and potentially allow an attacker to take control" of the computer.
The fix is also urged for phone and tablet users of the Android operating system versions 4.x, 3.x and 2.x. (That accounts for nearly every Android phone currently in use.)
Adobe said last year that Flash wouldn't be coming to Android 4.1 or later. As NBCNews.com's Devin Coldewey wrote then, "Many websites still use Flash for media delivery or navigation, and have yet to update to HTML5 and other, more future-oriented, standards."
The patch for computers is available here; Android users are instructed to check their Flash version by going to Settings > Applications > Manage Applications > Adobe Flash Player x.x. The latest Flash version for Android 4.0 is 11.1.115.36; and for Android 2.x and 3.x is 11.1.111.31.
One of the Flash attacks "is targeting aerospace and other manufacturing companies, and is being delivered via infected Microsoft Office documents," Michael Mimoso, of Kaspersky Lab, wrote on the company's Threatpost blog Friday.
Those attacks use spear-phishing emails — essentially booby-trapped emails designed to infect a user's computer of phone — to "trick victims into opening Word file attachments that are carrying an embedded .SWF Flash Player file," Mimoso wrote.
"The SWF files used in the exploit work only against certain versions of Flash and operating systems; they also reference a character in the video game 'Dishonored' called Lady Boyle in the name of the action script embedded in the SWF file."
Jaime Blasco, of AlienVault Labs, wrote on that company's blog that one of the files was using the 2013 IEEE Aerospace Conference schedule "as a lure to trick the user into opening the file."
Web-based attacks playing to the Flash vunerability, in contrast, are mainly "drive-by downloads where attackers lure victims to a website hosting the malicious Flash file," Mimoso wrote. "Adobe said the attacks are limited to Firefox or Safari, and can also be delivered via Word document attachments."
If you have questions about Flash, Adobe's online community forum is one resource to find more answers. If you're not sure which version of Flash you're running or need to run, you can visit this Adobe page to check.
Check out Technology, GadgetBox, DigitalLife and InGame on Facebook, and on Twitter, follow Suzanne Choney.