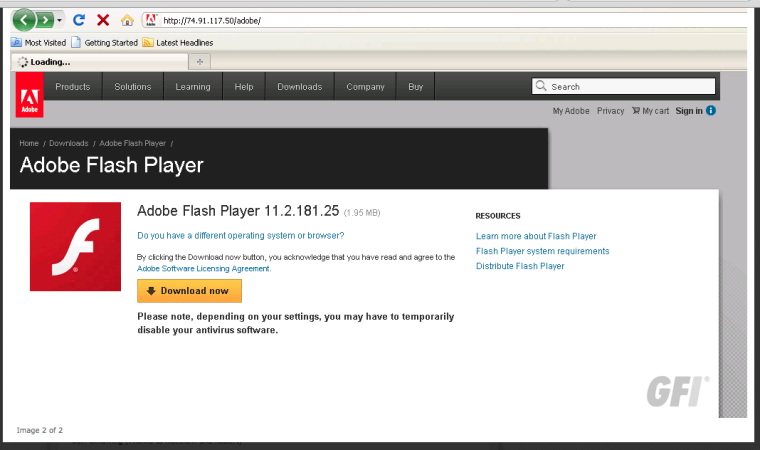
A new spam email campaign infects users' computers with a fake update for Adobe Flash Player — but all the victims will be watching is money drain out of their online bank accounts.
That's because the fake Flash update instead installs the Zeus banking Trojan, and then directs victims' computers to domains hosting more malicious software.
The infectious emails purport to come from the Better Business Bureau or the digital-faxing company eFax Corporate, security firm GFI Labs reported last week.
The Trojan comes aboard victims' computers by way of the Pony downloader, another malicious piece of code that simultaneously gives the Trojan access while stealing File Transfer Protocol-related passwords.
Zeus, possibly the most successful banking Trojan yet, breaks into bank accounts by logging the keystrokes that victims enter into their computers when conducting financial transactions online.
According to Kaspersky's Threatpost security blog, this scam is the most recent version of a phishing scam that already has infected computer users with a fake download for Google Chrome.
GFI said the malicious software is hosted at an address that's also home to several popular browser exploit kits used by hackers, including Blackhole, Medfos and Simda.
The address hosted at least five other compromised domains, GFI added.
Internet users can avoid falling victim to such scams by verifying email addresses and links. No matter what a link or address purports to say, right-clicking or mouse-hovering over the text often reveals the sender's or website's true identity.