An anonymous researcher used methods commonly employed in malicious hacking to get information on every IP address on the Internet, and has publicly released the results. Though he did it with good intentions — and created a database that may well prove useful to research — the project was definitely illegal.
The technical aspects of the research are explained in the paper itself, but the simplest explanation is this: The researcher began scanning IP addresses for devices that were more or less totally open to being logged into and modified, and then used those devices to scan further IP addresses.
It's a bit like he walked down the street, writing down each address then trying the doorknob. If it was open, he went in and convinced whoever lived there to join him in his data-collection quest — and soon his army of helpers had mapped the whole world.
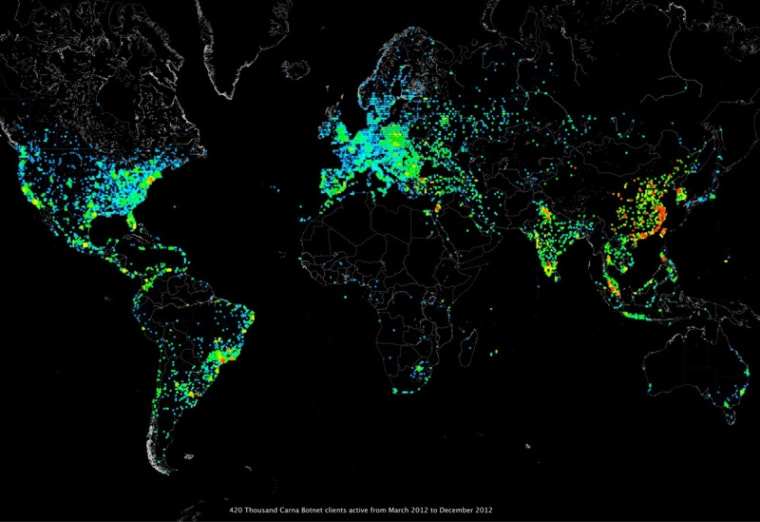
Within a day, he had a "botnet" of over 420,000 devices doing his bidding, though he writes that at least four times that number were accessible. Many of these devices were routers and random pieces of Internet-connected equipment, like appliances and printers. All were accessed by simply ascertaining their existence with a quick scan and then submitting the most common usernames and passwords, like "admin" and "default."
Working together, these devices could scan every IP address on the Internet in an hour or so, allowing for a very detailed breakdown of what parts of the Internet are active and when.
"This is most definitely illegal," Roel Schouwenberg, senior researcher at Kaspersky Lab, told NBC News in an email. "Even if the intentions are good, which we have no way of verifying. unauthorized access remains unauthorized access." Even if the compromised devices were thermostats or modems, "it doesn't matter if it involves a regular desktop computer or a router."
Although he was breaking laws, the hacker insists in the paper that he was careful not to disturb or break anything. His scanning program was not installed on anything that might be mission-critical or easily disrupted. And it only accessed devices that were absolutely wide open.
As proof of his benevolence, when his botnet encountered a rival botnet that was clearly made for malicious purposes, he added a bit of code to protect the machines against it.
Carna, as the botnet was called by its creator, ran from June to October of 2012 and was apparently never detected. It has since been decommissioned, although the affected devices are likely still not secure and could be gathered up again by him or anyone interested in doing so.
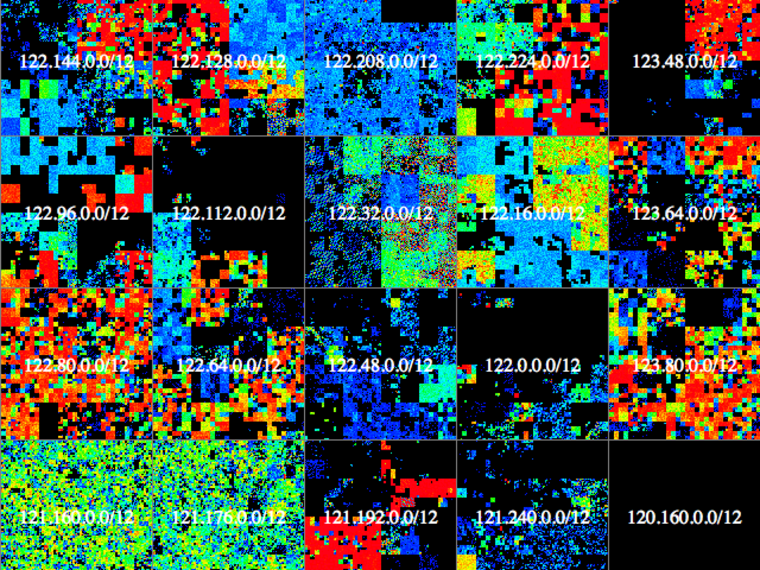
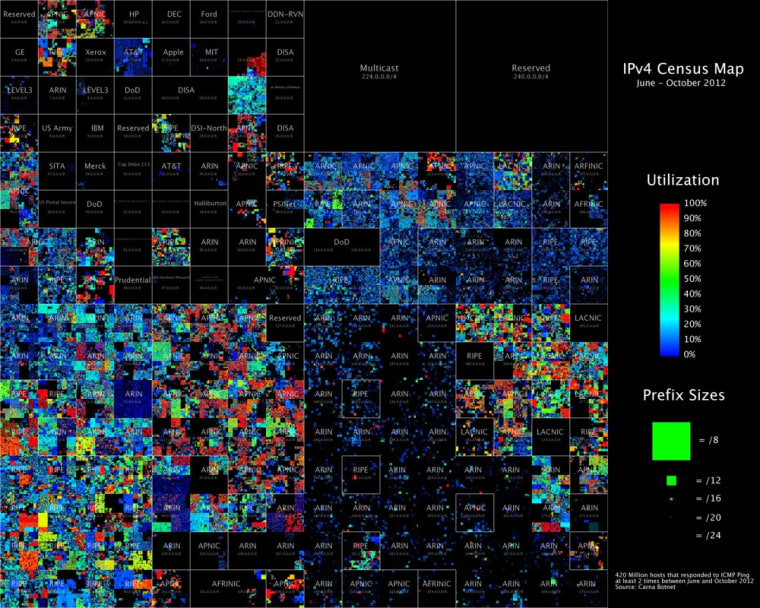
The enormous database is available for download — though at 9 terabytes, it's bigger than any single hard drive on the market. The hacker found some interesting things, like areas of the Internet that should be empty but aren't, and a daily rhythm to Internet devices going on- and offline. The raw data of this morally dubious but unquestionably effective botnet will surely be valuable to security and networking experts all over the world.
While the full paper contains a lot of very technical information and descriptions of code, it is fairly readable even to a lay person and contains some attractive visualizations, some of which you see here.
Afraid you might be compromised? Locking down your router or printer is easy: Check the manual or do a quick search for your model number and follow the instructions to change the login and password to something more secure.
Devin Coldewey is a contributing writer for NBC News Digital. His personal website is coldewey.cc.