If you got an email from the Centers for Disease Control and Prevention or the World Health Organization about the coronavirus outbreak, would you read it? Maybe click on a link? Cybercriminals are counting on it.
The outbreak is a dream come true for criminals who will use it as basis for email attacks designed to snag personal information, steal money and infect computers with malware.
Malicious email linked to the coronavirus first appeared in early February, making it one of the first big phishing campaigns of the year.
“A global health disaster like this creates a golden opportunity for fraudsters, as there is no population or demographic that is not paying attention. As a result, the potential for impulse clicking is higher than normal,” said Adam Levin, a digital security expert who is chairman of CyberScout, a data security firm, and the author of “Swiped: How to Protect Yourself in a World Full of Scammers, Phishers and Identity Thieves.”
Full coverage of the coronavirus outbreak
The bogus emails look legit
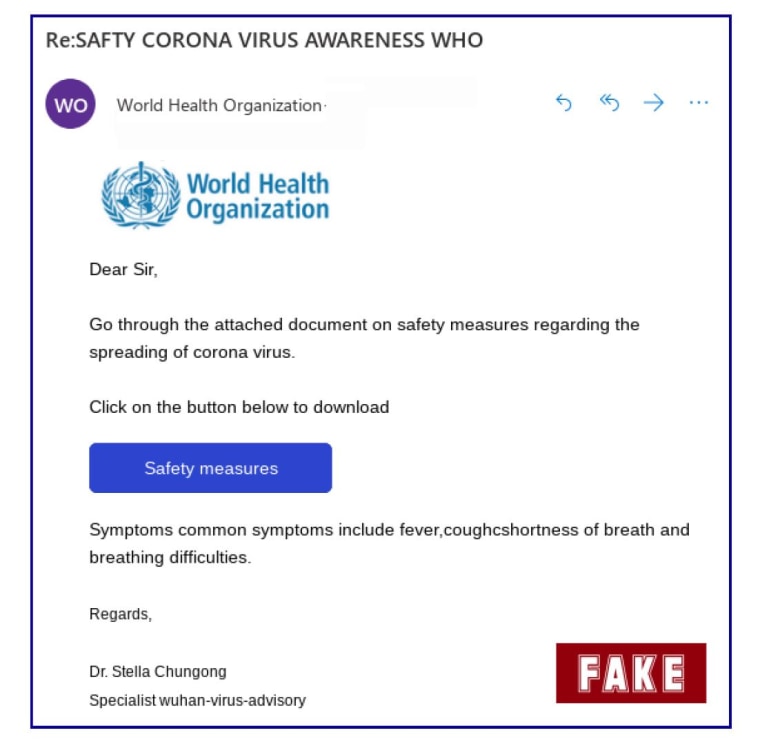
The email above may look legit, but it is not from the World Health Organization. Those who click on the link wind up on a site created by criminals to steal email credentials.
Sophos, a U.K.-based internet security company, recently warned about bogus emails that appear to be providing information about coronavirus “safety measures” from the WHO.
Chester Wisniewski, a senior security adviser at Sophos, said the email is short and simple, something that could be created in just a few minutes.
“The message doesn’t need to be very complicated because there’s so much interest and concern about this virus,” he said. “All the criminals need you to do is click on a link and land on a site they control, so they can steal your email password. With that, they can take whatever they want.”
With this current phishing attack, the fraudsters are designing their emails to look like they’re coming from the CDC or the WHO. They typically have an attention-grabbing subject line, such as “Coronavirus outbreak in your city (Emergency)” and often include the agency’s logo — cut and pasted from the real website — to add credibility.
At first glance, the sender’s email address appears to be legitimate, for example cdc-gov.org or cdcgov.org. The crooks create domains that are very close to the real CDC site — cdc.gov — making the deception easy to miss.
One of the bogus emails spotted by Kaspersky, a global cybersecurity company, claims the CDC has “established a management system to coordinate a domestic and international public health response.” Recipients are urged to click on a link that looks like a legitimate cdc.gov webpage to get an “updated list of new cases around your city.”
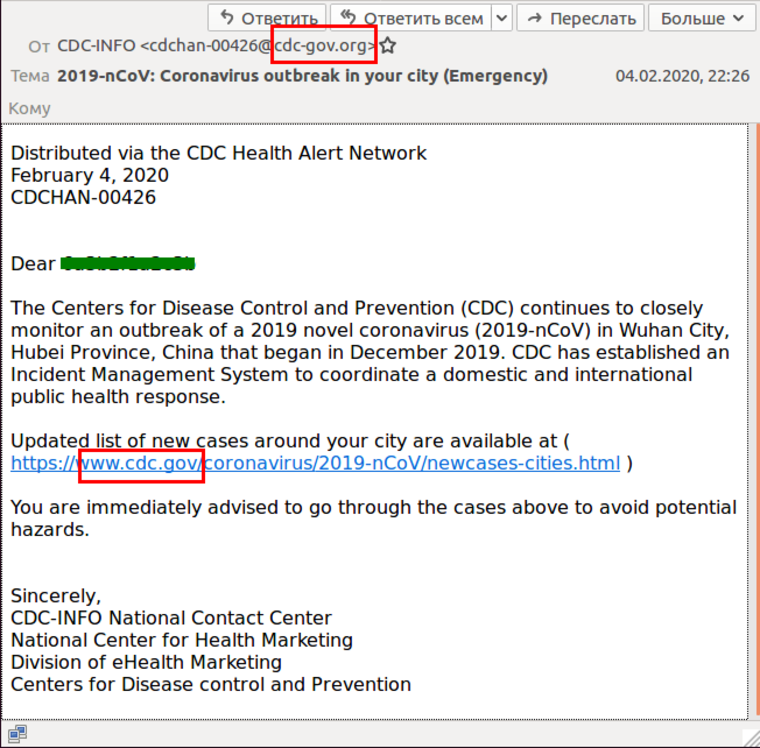
This bogus email is not from the CDC. It’s another phishing attack designed to harvest user names and passwords from people who click on the link.
Even though the link looks like it will take you to a CDC.gov website about the coronavirus, it will not.
You land on a fake Microsoft Outlook login page, created by the crooks to steal user names and passwords. Criminals control this fake Outlook page. There is no reason to provide login credentials to visit a public website, such as the CDC.
“Once they capture your login credentials, they can use them to get access to your email account and look for anything worth stealing,” said David Emm, principal security researcher at Kaspersky, in an interview from London.
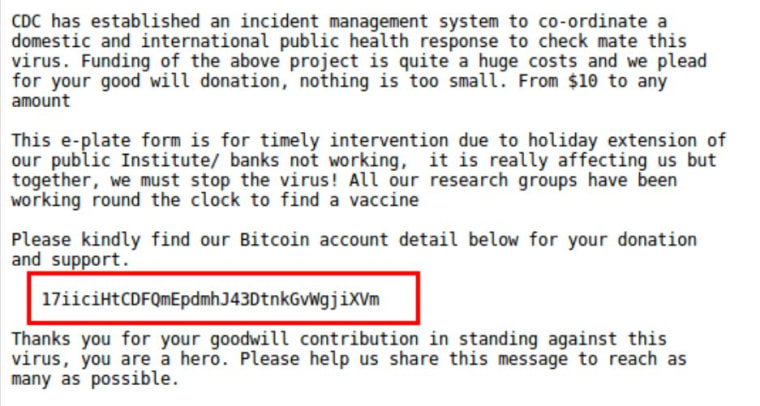
Kaspersky researchers have spotted another malicious email made to look like it was sent by the CDC. This one asks for a donation via Bitcoin to help fund its “incident management system” that’s coordinating the response to the coronavirus.
“Funding of the above project is quite a huge costs and we plead for your good will donation, nothing is too small. From $10 to any amount,” the message reads, typos intact.
Of course, the CDC is a government agency that’s funded by U.S. tax dollars, so it does not solicit for individual donations — and it certainly doesn’t accept Bitcoin.
Some cybercriminals are also using the coronavirus to spread malware. Links in the email that are supposed to go to educational material will infect your computer.
Security experts tell NBC News BETTER that if these initial phishing attacks are successful, the volume of these attacks will quickly multiply.
How to protect yourself from coronavirus scams
You need to be skeptical of any email that asks you to click on a link or open an attachment — even when the email seems legitimate.
In most cases, you can probably get the information you need by typing in the URL yourself. For the latest on the coronavirus outbreak go directly to the CDC website.
The security team at Sophos has these tips:
- Don’t be taken in by the sender’s name. Scammers can put any name they like in the “from” field.
- Look out for spelling and grammatical errors. Not all crooks make mistakes, but many do. Take extra time to review messages for telltale signs that they’re fraudulent.
- Check the URL before you type it in or click a link. If the website you land on doesn’t look right, steer clear. Do your own research and make your own choice about where to look.
- Never enter data that a website shouldn’t be asking for. A site that’s open to the public, such as the CDC or WHO, will never ask for your login credentials.
- If you realize you just revealed your password to impostors, change it as soon as possible. The crooks try to use stolen passwords immediately, so the sooner you change your password, the more likely you are to stop them for doing anything malicious.
- Never use the same password on more than one site. Once crooks have a password, they’ll try it on every website where you might have an account, to see if they can get lucky.
- Turn on two-factor authentication (2FA), if you can. Yes, it’s a slight inconvenience to enter a six-digit code when you want to long on, but it’s a huge barrier for the crooks. With 2FA, a stolen password, by itself, is useless to them.
Kaspersky has 10 tips to protect yourself from phishing attacks on its website.
UPDATE: Scammers have now taken things to the next level, sending out bogus emails designed to infect your computer with malware, according to Sophos.
The email purports to be from the “CDC Health Alert Network” with updated information about “outbreak safety measure in your neighborhood.” Open the attachment and it downloads ransomware that will lock-up your system and demand payment for the decryption key.
Remember: Health agencies are not sending emails about the coronavirus. To get the latest information, you need to visit the CDC website or your state or local health department.
More ways to protect yourself from scams
- Looking for love online? Romance scammers steal your heart to steal your money
- A former conman shares tips for protecting yourself from fraudsters
- How to protect yourself from business email scams
- How to spot (and avoid) these Facebook and social media prize scams
- Use payment apps like Venmo, Zelle and CashApp? Here's how to protect yourself from scammers
Want more tips like these? NBC News BETTER is obsessed with finding easier, healthier and smarter ways to live. Sign up for our newsletter and follow us on Facebook, Twitter and Instagram


