The Mydoom computer virus continued to flood Internet users with stray e-mails on Thursday, amid growing consensus that the malicious program had become the fastest-spreading e-mail virus ever. Meanwhile, as researchers investigated a variant of the virus that takes aim at Microsoft's Web site, the software giant issued a $250,000 reward for information leading to the virus author's arrest.
“This worm is a criminal attack,” said Brad Smith, general counsel at Microsoft. “Its intent is to disrupt computer users, but also to keep them from getting to anti-virus locations and other sites that could help them. Microsoft wants to help the authorities catch this criminal.”
The SCO Group, the target of the original version of Mydoom, on Tuesday offered a similar $250,000 award. The virus is designed to flood SCO's Web site with requests in an attempt to crash its server, starting Feb. 1. SCO, which has been targeted in other recent attacks, is in the middle of a prolonged fight with Linux users, but there is no evidence directly linking that argument to the attacks.
The worm was first released on Monday and quickly spread like wildfire across the Internet. On Wednesday, it prompted the first use of a new cyber alert system put into place by the Department of Homeland Security.
Antivirus firm MessageLabs said that by Thursday, it had trapped over 5.5 million copies of the infected e-mail headed for its clients. At one point, one in every 12 e-mails were laced with the worm, the firm said. By comparison, last year's SoBig virus outbreak peaked at an infection rate of 1 in 17 e-mails.
Both Network Associates Inc. and F-Secure Corp. say Mydoom -- also known as Novarg -- has generated more traffic than any e-mail worm in history.
On Thursday, Network Associates spokesman Vincent Gullotto said as many as 500,000 computers had been infected at some point by the worm, and 26 percent of its customers had reported receiving the worm, an all-time high.
"It's sustaining some potency and it's still moving," he said. "Although companies I talk to today say they are a little less worried than yesterday."
Other companies offered similar staggering statistics. F-Secure said that at one point, 20 to 30 percent of all e-mail traffic worldwide was generated by the worm. America Online spokesman Andrew Weinstein said his company trapped 9 million Mydoom-laden e-mails headed for its customers on Tuesday. Earthlink spokesman Dave Blumenthal said 14 percent of all e-mail headed for his firm's customers were infected.
But comparisons with older infamous worms like LoveLetter and the Melissa virus, which actually caused many corporations to shut down their e-mail systems, were hard to make. Drastic measures like turning off e-mail servers kept down the total number of stray e-mails created by both LoveLetter and Melissa. However, antivirus experts say that while Mydoom generated more e-mail traffic, Melissa and LoveLetter had greater impact on corporate operations, since few companies were forced to turn off all their e-mail this time around.
Could attack slow Internet?
In addition to attacking Microsoft and SCO, the new version also tries to block victims from reaching antivirus Web sites. It also blocks ads served by about a dozen advertising network sites, including Ad.Doubleclick.net and ads.Fastclick.net.
While the variant targeting Microsoft has infected very few machines, there is concern that as many 200,000 computers remain infected with the original Mydoom. If they all attack SCO's Web site Sunday, the resulting traffic could impact the Internet, Gullotto said.
This is the third time Microsoft has offered a reward for help catching virus writers. In November, the company announced it was creating a $5 million fund for offering rewards. At the same time, it offered $250,000 for information leading to the arrest of the author of the SoBig virus, and another $250,000 for information about the author of MSBlast, another malicious program released last year.
Christopher Budd, a security program manager at Microsoft, confirmed the software giant is investigating the situation. He could not discuss steps the firm might take protect its Web site.
"We take steps every day to protect our Web site. Like many major Internet sites, we are under attack on a daily basis," he said. "We are daily taking steps and countermeasures to keep our site up."
While the attack on Microsoft is set to begin Feb. 1, a bug in the code will prevent the stream of traffic from beginning until Feb. 3, said Tony Magallenez, a spokesman for F-Secure, Inc.
The variant was likely written by a different author than the original worm, Magallanez said. The initial worm was designed to avoid sending e-mail to certain domains, including Microsoft, Google, and various .mil, .edu, and .gov domains -- perhaps to avoid raising the ire of those institutions. Since the variant directly attacks Microsoft, the two worms seem to be at cross purposes, Magallenez said.
"It looks like somebody got a hold of the first worm and altered it slightly and re-released it," he said.
Attached text file trick
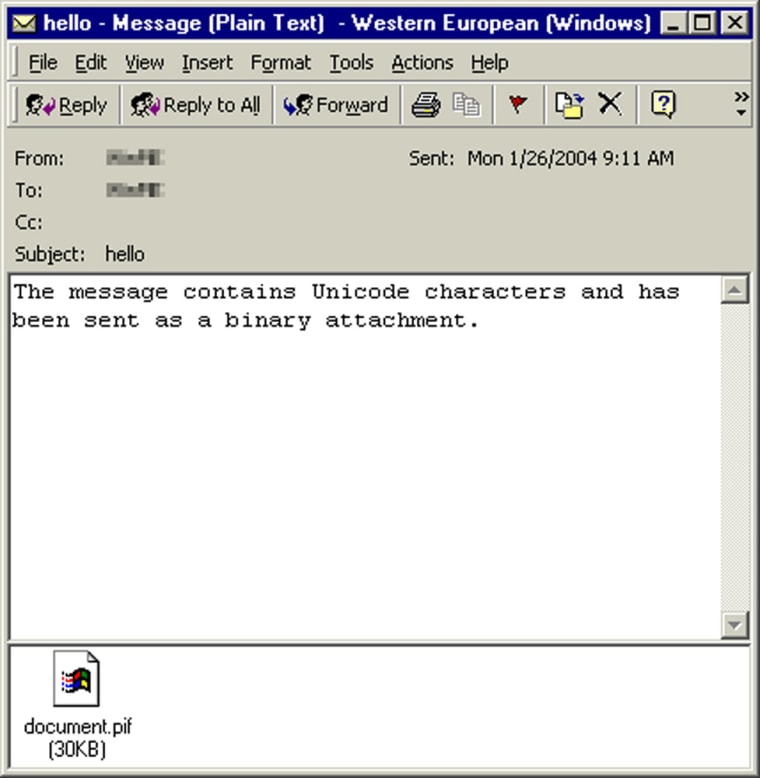
Mydoom is effective because it arrives posing as a harmless text file containing an e-mail message. It often claims to be from a colleague or friend and offers the believable explanation that the original message had to be translated into a plain-text file for delivery. The attachment often displays the notepad icon. The message body often reads: "The message cannot be represented in 7-bit ASCII encoding and has been sent as a binary attachment."
Other variations say: "The message contains Unicode characters and has been sent as a binary attachment," or "Mail transaction failed. Partial message is available." In any case, the message urges recipients to open the attached file, which is really an executable file, such as a zip file, that includes a malicious virus.
But the technical jargon was apparently enough to dupe plenty of e-mail users. Users who know text files are harmless are falling for the deception and clicking on the attachment at alarming rates, according to virus research Sharon Ruckman of Symantec Corp.
"People in the know think, 'It's safe for me to click on it,'" Ruckman said. "This is a pretty serious one. It's spreading very quickly."
The virus also fooled people by using random file names. The name of the attached file can be body.zip, document.zip, message.zip, readme.zip or text.zip. The subject line of the infected e-mail may include an innocuous phrase like "Hello" or "Server Report," though often it is simply left blank. Other possible subject lines, according to F-secure, include "hi," "Mail Delivery System," "Mail Transaction Failed," "Status," and "Error."
The attachment may be named document, readme, doc, text, file, data, test, message, or body, and it may arrive as one of several types of attachments: pif, scr, exe, cmd, or bat. Mydoom can also be spread by file swappers using the KaZaa network.
The worm itself can only infect Windows users, but because it's generating so many automated e-mail replies, Macintosh and Linux users can suffer fallout from the outbreak, too. Much like the SoBig virus, Mydoom "spoofs" e-mail addresses, so return e-mails, such as "undeliverable" notices, are being sent to unsuspecting third parties around the Internet.