While being invisible on the Internet is about as possible as being invisible in real life, a few easy changes of habit can make you a more elusive target for advertisers, intrusive social networks and possibly even the NSA and friends. While these are measures anyone can take, please note, they won't necessarily provide total anonymity or protection from hackers. They'll just keep much of your everyday Internet activity from being recorded and tracked.
1. Use private browsing windows
Whether you're looking up engagement rings or a sensitive medical issue, there are plenty of reasons to go off grid temporarily. All major browsers offer a mode that neither loads nor stores any information about you on any sites — when you finish, it'll be as if the session never occurred on your computer, and visited sites won't remember much (just whatever they can glean from your home network's IP address).
Look for the option in the main menu of your browser. In Chrome it's "Incognito," in Firefox it's "Private Window," and in Internet Explorer it's "InPrivate Browsing."
2. Adjust your preferences!
Almost every app, service, game — anything you have to download or sign up for — has a preferences or options menu. Go through and uncheck anything that you're not totally okay with.
Sending anonymous usage data? Can it really be anonymous? Uncheck. Geotag pictures? You can always add location later. Uncheck. Check for updates on startup? Do you really want companies knowing exactly when and how often you use their stuff? Uncheck. How much information you volunteer is up to you, but usually you have to opt out rather than in.
3. Download browser plugins
You can modify your browser to reject dubious activity on the Web. Here are two of the best add-ons:
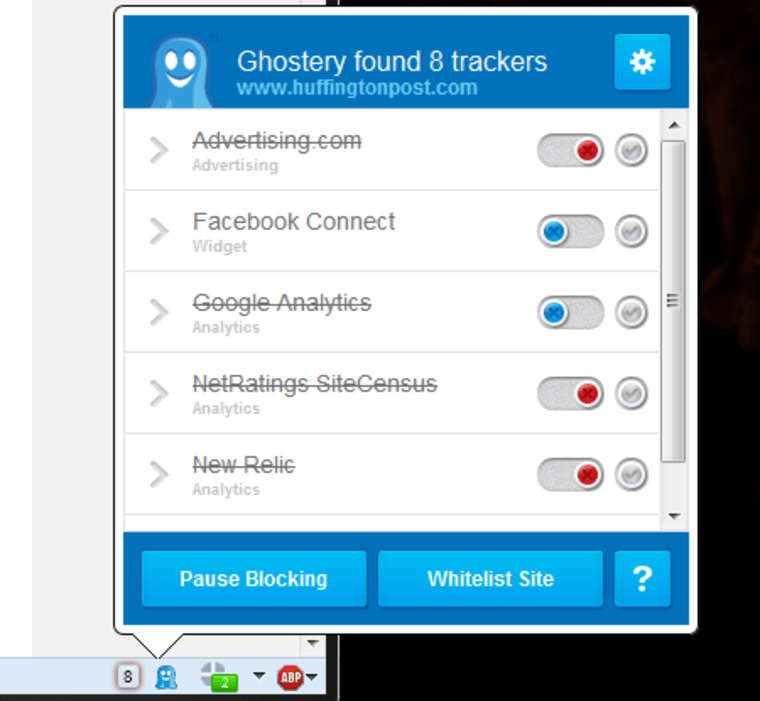
Ghostery: Creeped out by Facebook widgets showing which of your friends likes the site you're on? Ghostery allows you to turn on and off everything from social widgets to tracking cookies.
HTTPS Everywhere: This useful tool from the Electronic Frontier Foundation makes sure you're connecting with websites at the highest level of security supported, so it's more difficult for snooping software to see what you see. It's especially good if you use public Wi-Fi a lot.
4. Use false identities
Unless your real name or address is actually necessary for a service you're signing up for (e.g. job recruitment or banking), there's no reason to provide it. Put in "Jane Doe" or "Bill Clinton" instead — it can't hurt anyone and it may save you from unwanted communication (even in your real mailbox).
It's not just your name that you should be careful with, either. Your username is often public-facing, and can be used to track you as well. Are you "SeattleGuy1949" on Gmail, AIM and assorted support forums? Advertisers (and hackers) will be able to connect the dots. Make up unique names, and let a password manager — or a pad of paper — take care of remembering them.
Lastly, there's no reason to have everything go to your main email address. Email is free, so keep one for personal correspondence and a spare for lists and sign-ups. Some email services, such as Microsoft's Outlook.com, let you add additional email addresses — and even temporary ones — for transactions you want to keep one-sided.
5. Choose services built for anonymity
If you use Google, there is a 100 percent chance that you're being tracked for ads. Even the new Yahoo mail has ad-tracking on by default — though, like Gmail, that can be deactivated. If you use Microsoft's SkyDrive, Apple's iCloud or other cloud storage services, your content may be passively monitored for illegal material like child porn. While monitoring tends to be lawful and non-intrusive, many don't like the idea of their private lockers being rummaged.
Try these alternatives to the usual suspects:

DuckDuckGo search engine provides solid results, totally anonymously. Unsurprisingly, the site's traffic has skyrocketed since the PRISM story broke.
Hushmail works like any other webmail, but offers strong encryption both while your emails are in transit and when they're stored. The host company won't look unless a court order forces them to. (Note: If you love your current webmail, you may be able to deactivate the ad-tracking, so have a look in the preferences before jumping ship.)
SpiderOak cloud storage is totally encrypted — only you know what you put there. If 2GB is enough for your private files, sign up for a free account and you can be reasonably sure that your data is secure.
6. Take extreme measures
If you want to go further down the rabbit hole, you'll need to put in some serious time looking up things like VPNs and proxies, TOR, PGP, TAILS and local encryption. These powerful tools aren't easy to use, and are often employed for evil as well as good, so you're on your own there.
That said, for most of the everyday surveillance we're subjected to as we use Internet services and browse the Web, the rest of the above should help keep you undercover.
You can read about the leanest and meanest new technologies that protect your identity, here.
Devin Coldewey is a contributing writer for NBC News Digital. His personal website is coldewey.cc.