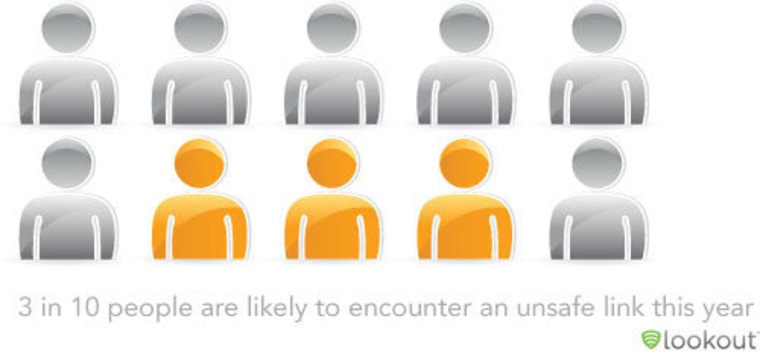
More than ever, Android and iPhone smartphone users need to be vigilant over their digital appendages, with as much as three out of 10 people likely to encounter an unsafe link this year, according to a recently released report.
Lookout, a smartphone security company that monitors apps on Android, Blackberry and Windows Mobile, issued the "Lookout Mobile Threat Report" last night and found Android users are two and a half times as likely to encounter malware today than 6 months ago, with half a million to one million people affected by some kind of malicious code in the first half of 2011.
Even more alarming: Android apps infected with malware shot up from 80 apps in January to more than 400 apps by June.
Lookout gathered the data for its report through its " Mobile Threat Network, "which includes the world’s largest database ofapplications and aggregates detection results from mobile devices throughout the world."
Smartphones are rapidly becoming a must-have, Lookout points out, "with sales expected to increase from 300 million in 2010, to 650 million in 2012." And Android, with more than 200,000 apps, doesn't have the necessary armor — yet — to repel the multitude of attacks upon it. But Apple's iOS is also under attack, and malware has slipped through over their fortress too.
The report concludes that "both web-based and app-based threats are increasing in prevalence and sophistication," and that "attackers are deploying a variety of increasingly sophisticated techniques to take control of the phone, personal data, and money. Additionally, malware writers areusing new distribution techniques, such as malvertising and upgrade attacks."
App-based threats come in the guise of terms like malware and spyware, while web-based infiltration arrive through phishing scams, drive-by-downloads and browser exploits. Tapping into open networks also leaves users vulnerable, with Wi-Fi sniffing allowing those up to no good to steal info from those using unsecured local wireless networks.
Lookout warned of one particular malware writer, GGTracker, that should send shivers down any smartphone user's back.
First, it is one on the first pieces of Android malware we’ve seen to-date that engages in malvertising to trick users into visiting a malicious web site. Second, the malicious website convinces people into installing malware by convincingly imitating the Android Market and beginning a drive-by-download. Third, it is one of the first known instances of Android malware specifically targeting U.S. users by silently charges money to users’ phone bills when it is installed, charging $10 per service. Previously, we had only seen this type of malware on Android target China and Russia.
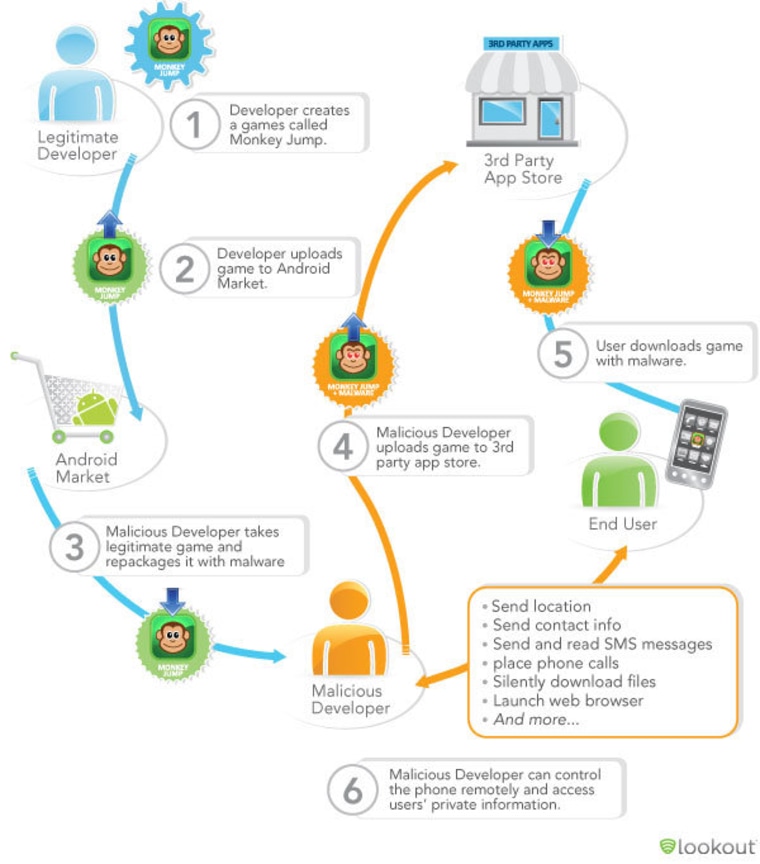
Back in March, more than 250,000 Android users were compromised in an unprecedented mobile attack when they downloaded malicious software disguised as legitimate applications from the Android Market — what is known as repackaging (see infographic above). More than 50 applications were infected with the DroidDream malware.
Lookout gives this blow-by-blow of the security measures already in place for Android, which also reveal its Achilles heel:
In the case of Android, Google regularly produces updates to fix security vulnerabilities on the Android OS within days of discovery and pushes the fixes into the Android OpenSource Project (AOSP). Next, it is up to device manufacturers to produce a device specific firmware update incorporating the vulnerability fix, which can take a significant amount of time if there are proprietary modifications to the device’s software. Device manufacturers typically pull the patch from the AOSP repository, merge in theirmodifications, and produce a new firmware update. This process is complicated by the fact that a single device model may have a large number of updates to support carrier specific customizations. Once a manufacturer produces a firmware update, it is up to each carrier to test it and deploy the update to users. For users, the process to install an update is rather simple — they typically receive the update over-the-air (OTA) and confirm its installation.
That doesn't mean Apple fanboys (and girls) are off the hook.
On iOS, security updates typically require Apple to produce a new firmware build, an operator to test the firmware build, and a user to sync with iTunes to install the patch. Because there are fewer parties in the iOS ecosystem — Apple, operators, and users — firmware updates are typically made available more quickly to a broad base of usersthan with Android. To apply an iOS firmware update, users must sync with iTunes.Unfortunately, many users simply plug their iOS devices into an outlet to charge themand rarely sync. According to one report, as many as 50 percent of iPhone users donot regularly sync with iTunes and thus are unlikely to receive critical security updates10.This failure to sync means that many users do not apply updates, even though they maybe available.
Lookout also reminded us of its Lookout App Genome Project report from February, which estimated that on iPhone 33.9 percent of free apps could access locations and 11.2 percent could access contacts on the device. On Android, they found 28.2 percent of free apps in the Android Market could do the same with location, while 7.5 percent could tap into contacts.
Lookout offers these tips to stay safe:
- Only download apps from trusted sources, such as reputable app stores and download sites. Remember to look at the developer name, reviews, and star ratings.
- After clicking on a web link, pay close attention to the address to make sure it matches the website it claims to be if you are asked to enter account or login information.
- Set a password on your mobile device so that if it is lost or stolen, your data is difficult to access.
- Download a mobile security tool that scans every app you download for malware and spyware and can help you locate a lost or stolen device. For extra protection, make sure your security app can also protect from unsafe websites.
- Be alert for unusual behaviors on your phone, which could be a sign that it is infected. These behaviors may include unusual text messages, strange charges to the phone bill, and suddenly decreased battery life.
- Make sure to download firmware updates as soon as they are available for your device.
More stories:
- Malware infects more than 50 Android apps
- 25 percent use smartphones, not computers, for majority of Web surfing
- Creepy Android malware records your phone calls
Check out Technolog on Facebook, and on Twitter, follow Athima Chansanchai, who is also trying to keep her head above water in the Google+ stream.