Data breaches are down almost 25 percent this year — but it's no cause for celebration: Cyber thieves have simply changed their game, and are now holding your data ransom instead of selling it.
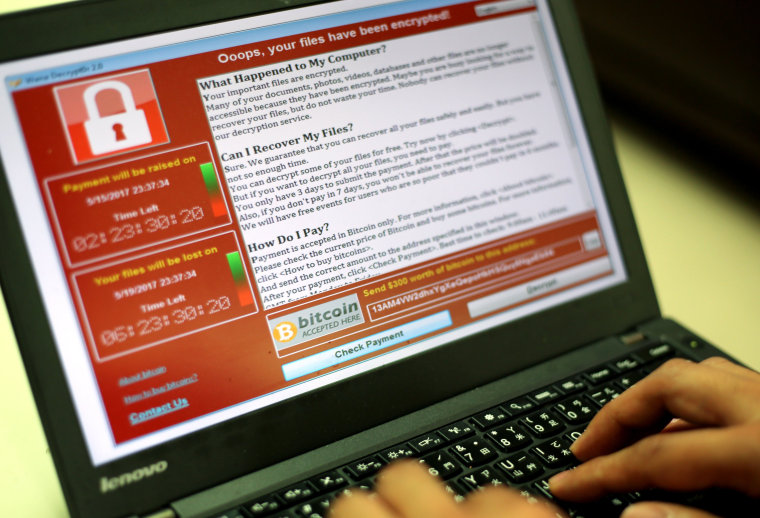
Cyberattacks such as WannaCry, NotPetya and Bad Rabbit “caused chaos across industries without compromising records,” noted the new IBM X-Force Threat Intelligence Index 2018, released last week. Global losses from WannaCry last year — including direct payments, downtime, and other business impacts — are estimated at more than $8 billion, according to a report by Reinsurance News.
“The hackers are just following the money,” said Paul Griswold, director of strategy and product management with IBM X-Force. “And from their perspective, ransomware is hopefully more profitable. Rather than having to steal records and then sell those records, they can just lock up your data with ransomware and get money directly from you.”
Criminals have so much compromised data available to them on the black market right now that it’s getting harder for hackers to monetize the records they steal, digital security experts tell NBC News. It’s simple supply and demand: The glut of stolen information has reduced the value of new stolen records.
“As a criminal, I would much rather simply compromise your organization, lock up your files, collect tens of thousands of dollars in a matter of a day or two, rather than try to glean all of your customers' data, find a willing buyer for it and wait to get paid. The economics just make much more sense,” said Al Pascual, head of fraud and security at Javelin Strategy & Research.
Here’s the rub: Even if you pay the ransom, there’s no guarantee you’ll get the key to decrypt your files. Sometimes ransomware can’t be unlocked, if it’s not designed with a key, said Pascual. That’s why it’s critical to be prepared for the worst by backing up important files.
Humans are the weakest link
Successful cybercriminals were able to take advantage of human error and mistakes in infrastructure configurations to launch their attacks last year. Hackers are finding and exploiting misconfigured cloud servers and network backups to harvest both personal information and corporate secrets.
These infrastructure mistakes were responsible for exposing nearly 70 percent of all compromised records tracked by IBM X-Force in 2017. That’s more than 2 billion records, an increase of 424 percent from 2016.
“As more and more organizations move their stuff to the cloud, they're sometimes doing it a bit more hastily than they should be doing,” Griswold told NBC News. “And as a result, you're running into situations where people are moving their applications there, but not necessarily bringing along their security policies for the ride. As a result, you have these misconfigurations that can lead to the exposure of tons of records.”
Phishing attacks — tricking users into clicking a malicious link or opening an infected file — remain a serious threat, IBM found. They’re responsible for more than one-third of inadvertent activity that leads to a security event. Often, this is how the hackers gain access to cloud storage. A single phishing attack in August 2017 cited in the report involved the use of a botnet to distribute 22 million spam messages in just two days.
Larry Ponemon, chairman and founder of the Ponemon Institute, a privacy research firm, isn’t surprised by this finding.
“A number of organizations are having a hard time with cyber-hygiene, getting people to just do the basics, like not sharing passwords,” Ponemon told NBC News. “It’s now more important than ever for people within the organization, the average-rank-and file employee, to do what's necessary to protect the company’s sensitive data, including their customers’ personal information.”
Are you being targeted?
Big companies are the prime targets because they have more treasure to loot. For the second year in a row, financial services companies are at the top of the hit list. And, while they have invested heavily in cybersecurity technologies to protect themselves, the IBM study found that cybercriminals “focused on leveraging banking Trojans specifically targeting consumers and end users across the industry.”
For example, the Gozi banking Trojan, the most prevalent financial services malware, takes control of initial banking login screens and then prompts customers to enter other personal information that is then shared directly with the attacker. “The use of Gozi, considered to be run by a skilled cybercrime operation, highlights how organized crime is overtaking all other classes of actors in the financial malware-facilitated fraud scene,” according to the report.
Recent ransomware attacks have crippled major medical institutions, city governments — Atlanta, most recently — and police departments, including 911 emergency systems. These targets all provide critical services that cannot be offline, making them more likely to pay.
Anyone can have their computer system compromised — we all have information an identity thief can use or sell. Responding to the increasing threat, Microsoft announced last week that it has added new features to Office 365 home and office subscriptions that make it possible to recover files locked up by ransomware.
What's next?
A report from Cybersecurity Ventures predicts the annual global loss to the ransomware crime spree could hit $11.5 billion by 2019.
Security experts believe incident response, how an organization deals with a breach or other digital threats, should be where companies, government agencies and organizations focus their security resources.
“It is no longer realistic to beleve that we can prevent these attacks from happening, but we can be prepared to minimize the damage and recover quickly,” said Adam Levin, chairman of CyberScout and author of Swiped: How to Protect Yourself in a World Full of Scammers, Phishers and Identity Thieves.
“To do so we must know as quickly as possible that we have a problem and have a damage control program in place to restore systems and protect our people and our intellectual property,” said Levin.
Herb Weisbaum is The ConsumerMan. Follow him on Facebook and Twitter or visit The ConsumerMan website.