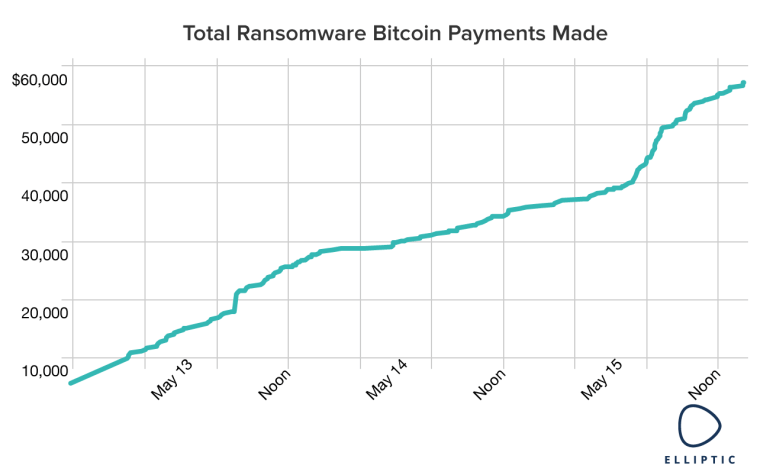
As of Monday evening, $57,282.23 in ransom had been paid to the hackers behind the "WannaCry" malware attack, which took down computers across the world Friday and over the weekend, according to Elliptic, a Bitcoin forensics firm tracking the event.
Payments have trickled in from around the world, including a relatively large payment that researchers believe originated from the Russian government or a Russian business.
The total will likely rise, however. As the chart below shows, payments increased Monday morning, days after the worst of the attack was slowed with a kill switch.
Payments have mostly originated from Europe, Russia, Korea, and Taiwan, according Chainanalysis, another firm that tracks Bitcoin transactions.
Paying the ransom will likely not save those infected, say cybersecurity researchers. Following payment, infected files are not automatically returned into the possession of the computer owner.
Related: 'WannaCry' Malware Cyberattack Slows, but Threat Remains
Instead, communication with the hackers overseeing the attack must occur. Then, an operator manually decrypts the files. Just sending the ransom gives the hackers "no idea if you've paid or not," said Jonathan Levin, co-founder of Chainanalysis.
In total, payments to cover about 190 computers have been made, a far cry from the approximately 300,000 infections believed to occur to date.
A major reason for the difference is that a kill switch — a way of stopping the malware from taking control of a computer — was discovered on Friday, slowing the malware's spread.
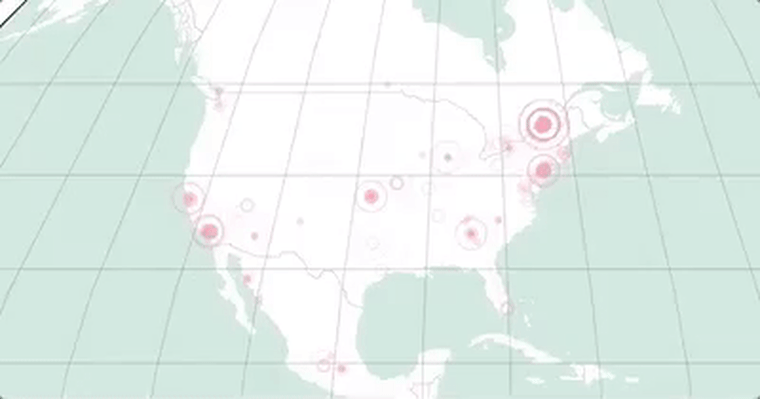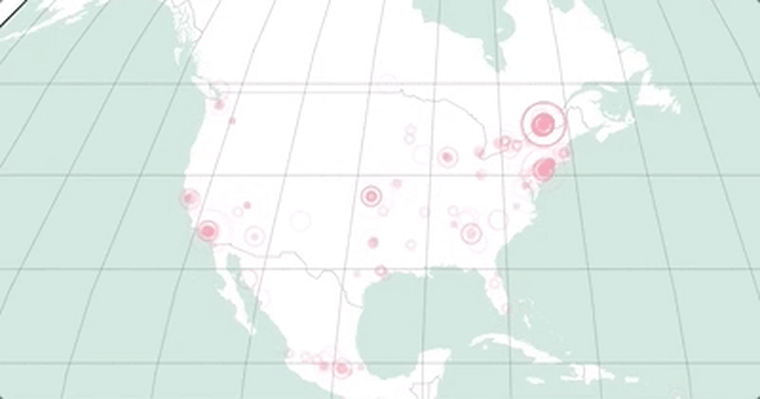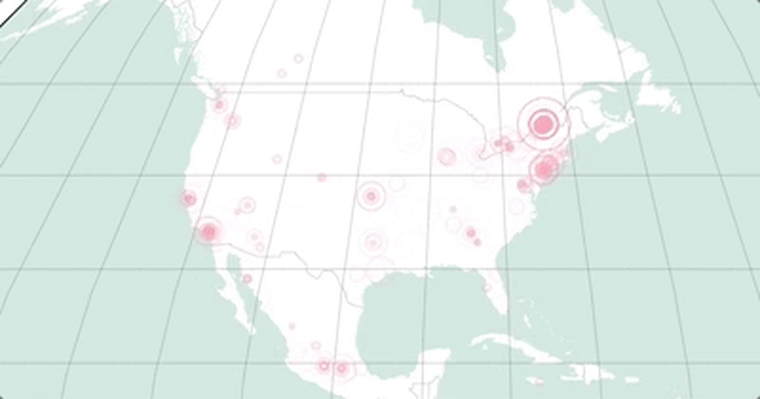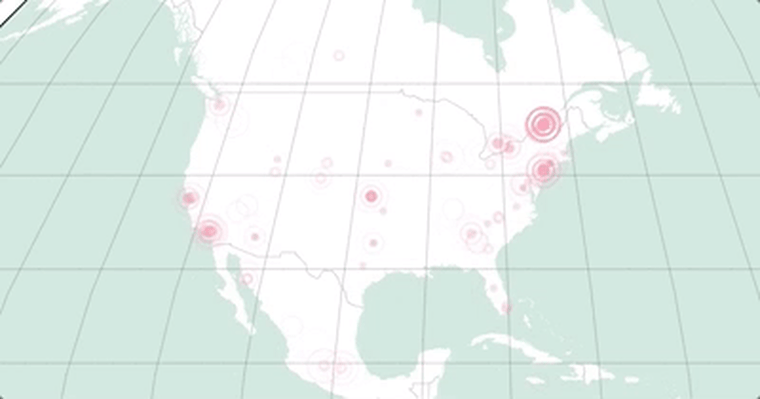
The map below, made from a dataset provided to NBCNews.com by MalwareTech, the security group that discovered the kill switch, shows how the malware was stopped on Friday.
Each location shows a computer that was infected but that did not have its files taken hostage because the kill switch prevented the attack. This map gives a general sense of how the malware spread.
The map shows a slight dip in malware preventions around 3 pm. The kill switch temporarily went offline at that time.